Clients are a Play:1 and a Play:3. Both clients were able to group and ungroup, stream music, and update firmware from the Android and Windows 10 clients. I didn’t experience any issues streaming music from Pandora or Amazon Music.
Aruba Instant 8.4+, 300 series APs
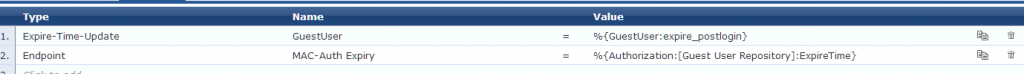
In the CLI, add the following:
airgroupservice Sonos
enable
id urn:schemas-upnp-org:service:GroupRenderingControl:1
id urn:schemas-sonos-com:service:Queue:1
id urn:schemas-upnp-org:service:AVTransport:1
id urn:schemas-upnp-org:service:RenderingControl:1
id urn:schemas-tencent-com:service:QPlay:1
id urn:schemas-upnp-org:service:GroupManagement:1
id urn:schemas-upnp-org:service:ZoneGroupTopology:1
id urn:schemas-upnp-org:service:DeviceProperties:1
id urn:schemas-upnp-org:service:MusicServices:1
id urn:schemas-upnp-org:service:AlarmClock:1
id urn:schemas-upnp-org:device:ZonePlayer:1
id urn:schemas-upnp-org:service:SystemProperties:1
id urn:schemas-upnp-org:service:ContentDirectory:1
id urn:schemas-upnp-org:service:ConnectionManager:1
id urn:schemas-upnp-org:service:HTControl:1
id urn:smartspeaker-audio:service:SpeakerGroup:1
id urn:schemas-upnp-org:service:VirtualLineIn:1
id urn:schemas-upnp-org:service:AudioIn:1
id urn:schemas-upnp-org:device:EmbeddedNetDevice:1
id urn:schemas-upnp-org:service:EmbeddedNetDeviceControl:1
Troubleshooting:
show airgroup blocked-queries
show airgroup blocked-service-id
Update 7/2/21
A new use case for getting Sonos came up recently for allowing SSDP (Sonos discovery/broadcast/multicast) traffic across different VLANs. In this use case, clients were on a separate subnet and VLAN while the Sonos speakers were on a different VLAN/subnet.
Hardware setup was Aruba Central managed gateways, 2930F switches, and Instant APs. At the time of this writing, I was running AOS Switch 16.10.14, Instant 8.7.2, and SD Branch 2.3 on the gateway.
The technical summary for getting Sonos to run on my lab is the following:
Setup and enable airgroup as shown above, and enable roaming across mobility domains if multiple APs are used.
Disable broadcast filtering on any SSIDs clients, including mobile devices running the Sonos App and the Sonos speakers themselves, are using to communicate.
Setup tunneled node on switch interfaces connected to APs. Config snippet on the my access is the following:
alias node “show tunneled-node-server state”
alias server “show tunneled-node-server”
jumbo ip-mtu 1566
jumbo max-frame-size 1584
tunneled-node-server
controller-ip CONTROLLERIPHERE
keepalive interval 1
exit
interface IDSHERE tunneled-node-server
vlan CLIENTVLANID
name “wlan-1”
jumbo
exit
vlan CLIENTVLANID
name “wlan-2”
jumbo
exit
vlan 30
tagged 1
name “iap-mgmt”
jumbo
exit
vlan 249
name “transit”
untagged 1
ip address dhcp-bootp
jumbo
exit
device-profile name “ArubaAP”
untagged-vlan 30
tagged-vlan WLANVLANIDs
allow-tunneled-node
allow-jumbo-frames
exit
device-profile type “aruba-ap”
associate “ArubaAP”
enable
exit
On the gateway, enable jumbo frames on the switch to switch uplink, set the port as untrusted, and apply a default AAA profile for the WLAN VLANs passed to the gateway.
Reference: Airheads Post